what is meek ? meek is a blocking-resistant pluggable transport for Tor
“Meek” is a bocking-resistant pluggable transport for Tor. It encodes a data stream as a sequence of HTTPS requests and responses. Requests are reflected via a hard-to-block third-party web server to avoid direct connections with a Tor bridge. HTTPS encryption hides recognizable byte patterns in Tor traffic.
Link to this: https://trac.torproject.org/projects/tor/wiki/doc/meek
The key trick that makes the system work is “domain fronting”: it communicates with a forbidden domain in a way that makes it look like you are communicating with a permitted domain. It works by placing the allowed domain on the “outside” of a request: in the DNS request and the SNI TLS extension; and the banned domain on the “inside”: in the host header of the HTTP request. The trick works with web services that ignore the SNI and process requests based on the host header. Google, with its App Engine infrastructure on appspot.com, is one of these services. A client that wants to communicate with a forbidden subdomain of appspot.com while appearing to communicate with www.google.com can run the client plugin program as follows:
meek-client --url=https://meek-reflect.appspot.com/ --front=www.google.com
The meek-client program alone has a recognizable TLS handshake. To obfuscate the TLS part of HTTPS connections, meek-client should be run with the --helper option, which points to a browser extension that has been set up separately. How it works: meek-client tells the browser which URL to request, the browser requests it and returns the payload to meek-client. The TLS implementation is that of the browser, so it fits in better with the permitted traffic. Browser extensions for Chrome and Firefox can be found in the chrome and firefox directories.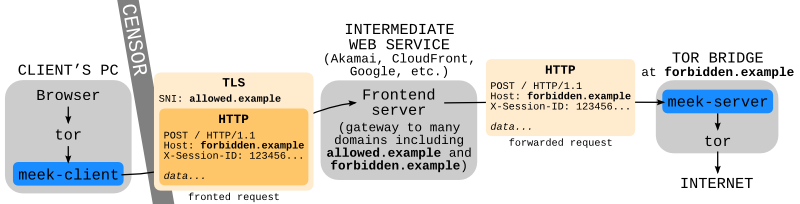
Source: meek - Wiki - Legacy / Trac - GitLab (torproject.org)
This diagram shows how data flows through different levels of encryption and protocol customization to circumvent censorship.
See details on what the protocol looks like at the byte level, both at the TLS level (the part that is visible to a censor) and at the HTTP level (the invisible layer that carries the data).